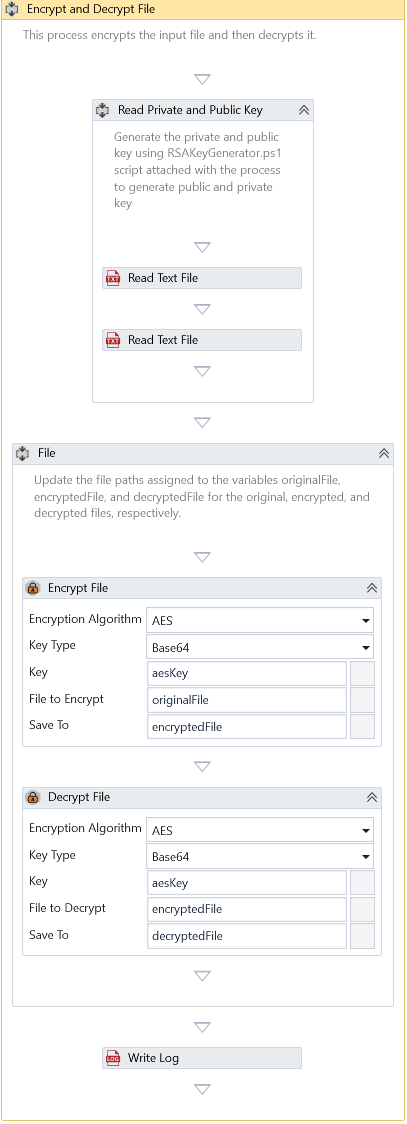
Decrypt File
Description
This activity decrypts the specified encrypted file using the chosen encryption algorithm, ensuring secure and confidential data processing.
Configuration
Configure the following properties in this activity's user interface to decrypt the encrypted file.
- Encryption Algorithm—Specify the encryption algorithm used. The table below details the algorithms supported by this activity.
| Algorithm | Description |
|---|---|
| AES | AES (Advanced Encryption Standard) is a widely used symmetric encryption algorithm known for its strong security and efficiency. It encrypts data in fixed-size blocks of 128 bits and supports key sizes of 128, 192, and 256 bits, offering flexibility for varying security needs. AES operates with an initialization vector (IV), typically 128 bits, in modes like Cipher Block Chaining (CBC). Renowned for its speed and robust security, AES is commonly used in secure communication and for encrypting data in storage applications. This is the default selection. |
| DES | DES (Data Encryption Standard) is a symmetric key encryption algorithm once the federal standard for encrypting sensitive information. It processes 64-bit data blocks using a 56-bit key (with 8 bits reserved for parity), making it vulnerable to brute-force attacks with current computing power. DES requires a 64-bit IV when used in CBC mode. Although now considered obsolete, DES laid the foundation for modern encryption standards. |
| TripleDES | TripleDES (3DES or Triple Data Encryption Standard) strengthens DES by applying the algorithm to each data block three times, using either two or three keys for a total key size of 112 bits (two-key) or 168 bits (three-key). Like DES, TripleDES operates on 64-bit data blocks and requires a 64-bit IV in CBC mode. While more secure than DES, TripleDES is slower and less efficient than modern algorithms like AES, and its usage is gradually declining. |
| RSA | RSA (Rivest-Shamir-Adleman) is an asymmetric encryption algorithm for secure data transmission and digital signatures. Unlike symmetric encryption, RSA employs a key pair: a public key for encryption and a private key for decryption. With key sizes starting at 1024 bits and typically 2048-bit or 4096-bit for modern applications, RSA offers a high level of security. It does not use an IV, as it encrypts smaller data chunks and relies on padding schemes like OAEP (Optimal Asymmetric Encryption Padding) to enhance security. |
- Key Type - Choose the type of the key provided. The following options are supported.
| Key Type | Description |
|---|---|
| Base64 | An encoded key format that converts binary data into ASCII text, commonly used for secure data transmission. This is the default selection. |
| Plain Text | A human-readable key used directly in encryption without additional encoding. |
- Key - Specify the key to decrypt the file.
- File to Decrypt - Specify the file's path to decrypt.
- Save To - Specify the path to store the decrypted file.
Properties
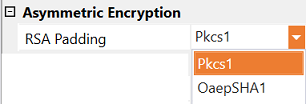
Asymmetric Encryption
- RSA Padding - Specifies the padding mode and parameters to use with RSA. The default is Pkcs1. The following options are currently supported.
| RSA Padding Mode | Description |
|---|---|
| Pkcs1 | A widely-used padding scheme where random bytes are added for security, but it has known vulnerabilities for chosen-plaintext attacks. This is the default selection. |
| OaepSHA1 (Optimal Asymmetric Encryption Padding) | Adds randomized padding and uses hash functions to enhance security; Uses SHA-1 as the underlying hash function for padding, which was commonly used but is now considered less secure due to SHA-1 vulnerabilities. |
Misc
- DisplayName – Add a display name to your activity.
- Private – By default, activity will log the values of your properties inside your workflow. If private is selected, then it stops logging.
Optional
- Continue On Error – Specifies if the automation should continue even when the activity throws an error. This field only supports Boolean values (True, False). The default value is False.
If you include this activity in Try Catch and the value of this property is True, it will catch no error during the execution of the project.
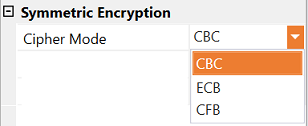
Symmetric Encryption
- Cipher Mode—Specify the mode in which the symmetric algorithm operates. The default is CBC. You can select one of the following options.
| Cipher Mode | Description |
|---|---|
| ECB (Electronic Codebook) | Each block is encrypted independently, making it fast but vulnerable to pattern attacks since identical plaintext blocks yield identical ciphertext blocks. |
| CBC (Cipher Block Chaining) | Each block is XORed with the previous ciphertext block before encryption, enhancing security by making identical plaintext blocks result in different ciphertext. This is the default selection. |
| CFB (Cipher Feedback) | Converts block cipher into a self-synchronizing stream cipher, allowing data encryption in smaller segments while chaining blocks for additional security. |
- Initialization Vector - Specify the initialization vector to salt the text.
An Initialization Vector (IV) is used in encryption to add randomness to the process. It ensures that even if the same plaintext and key are used multiple times, the resulting ciphertext will be unique each time. This prevents patterns in encrypted data, making it harder for attackers to deduce meaningful information. IVs are essential in block cipher modes (like CBC) to make encryption more secure and unpredictable.
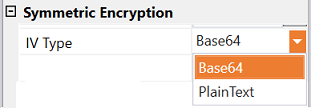
- IV Type - Specify the type of the IV (Initialization Vector) provided. The following options are available.
| IV Type | Description |
|---|---|
| Base64 | An encoded IV format that converts binary data into ASCII text, commonly used for secure data transmission. This is the default selection. |
| Plain Text | A human-readable IV used directly in encryption without additional encoding. |
- Padding Mode - Specify the padding mode and parameters to use with symmetric algorithm encryption. The default is PKCS7. You can select from the following options.
| Padding Mode | Description |
|---|---|
| PKCS7 (Public Key Cryptography Standards) | Adds bytes with values equal to the number of padding bytes needed; commonly used in block ciphers to ensure correct block length. This is the default selection. |
| ANSIX923 | Pads with zero bytes and ends with a byte that indicates the number of padding bytes, used primarily in financial cryptography. |
| ISO10126 | Uses random bytes for padding, with the last byte indicating the number of padding bytes; ensures data randomness but is now less commonly used. |
| Zeros | Fills extra space with zeroes; works well for data with fixed block sizes but can be ambiguous if data ends in zeroes. |
| None | Requires data to be the correct block size; often used with stream ciphers or in cases where the application manages padding. |
Example
Download Example